-
May 29, 2025

In the evolving digital landscape, websites are not just the virtual store for customers. It is the primary gateway for your businesses to enter your customers and engage with your products or services. Cybercriminals are using multiple techniques to steal the organization’s and customers data. That’s where Website Penetration Testing (also known as web app pen testing) is a controlled, ethical hacking process that identifies and exploits the vulnerabilities within the website. The intent of this process is to simulate real-world cyberattacks and identify exploitable vulnerabilities before malicious hackers do.
Importance of Penetration Testing for Websites
Website penetration testing helps organizations discover the unidentifiable flaws and vulnerabilities in their web application. It empowers teams to prevent attacks early and helps to take the necessary action to fix these vulnerabilities and hardened security. Website penetration tests also help ensure compliance with data security and privacy regulations by identifying how sensitive data might be exposed. This helps data remain secure and private while reducing the risk of leaks.
How is a Penetration Test Carried Out?
Website penetration testing starts with reconnaissance. During this phase, an ethical hacker gathers data about the target application or system to plan a simulated attack. Next, they focus on gaining and maintaining access using a set of software and hardware tools to execute SQL injections, brute-force attacks, and other techniques. These tools help identify remote access vulnerabilities.
The social engineering technique is one of the techniques used by hackers to break the security controls and take advantage to exploit the web application. The hacker will complete his test and cover his tracks, which includes removing the embedded hardware and other acts to avoid detection and they will leave the target application exactly how they found it.
Top 10 Web Application Security Requirements Every Business Needs to Know
Learn the top 10 web app security requirements to protect your business from breaches, data loss, and compliance issues.
Who Performs Penetration Tests?
There are certain security experts available in the industry who specialize in identifying the vulnerabilities that developers may have overlooked. Often, they called as ethical hackers or white hat hackers commonly involving these kind of activities. They are authorized to hack into systems or web applications for the purpose of improving security. These ethical hackers are experienced developers with advanced degrees and certifications in cybersecurity. Ethical hackers are not only capable of identifying security vulnerabilities, providing solutions to fix security flaws.
Types of Penetration Tests
When performing penetration testing, ethical hackers simulate attacks using specialized software tools. Automated penetration testing can efficiently cover all of these areas, providing fast and detailed reports. Depending on the tools and techniques used, penetration tests can be categorized into the following types,
- Closed Box Pen Test: Also known as a single-blind test, the tester is given no background information except the name of the target company and is expected to identify vulnerabilities independently with no leading info.
- Open Box Pen Test: The tester is provided with partial information about the company’s security framework before beginning their test.
- Covert Pen Test: Also called a double-blind test, this is conducted without the knowledge company employees including IT and security staff. The hacker must have a clearly defined scope and legal approval.
- External Pen Test: This test targets the company’s external technologies such as their web servers and websites. This is typically performed remotely without physical access.
- Internal Pen Test: Conducted from within a company’s internal network, this test evaluates potential liabilities from a malicious insider or compromised internal device.
Aftermath of Penetration Tests
After completion of the testing, the ethical hacker submits the comprehensive report to the organization’s security team. The report includes the roadmap for mitigating the vulnerabilities they found. Common security upgrades include rate limiting, DDoS mitigation, new WAF (Web Application Firewall) rules, and stricter input validation for external networks. For internal networks, it may include applying a zero-trust security model and possibly upgrading to a secure web gateway. If the ethical hacker used social engineering techniques, the organization’s security team should consider providing required training to their team members to secure their web application for future threats.
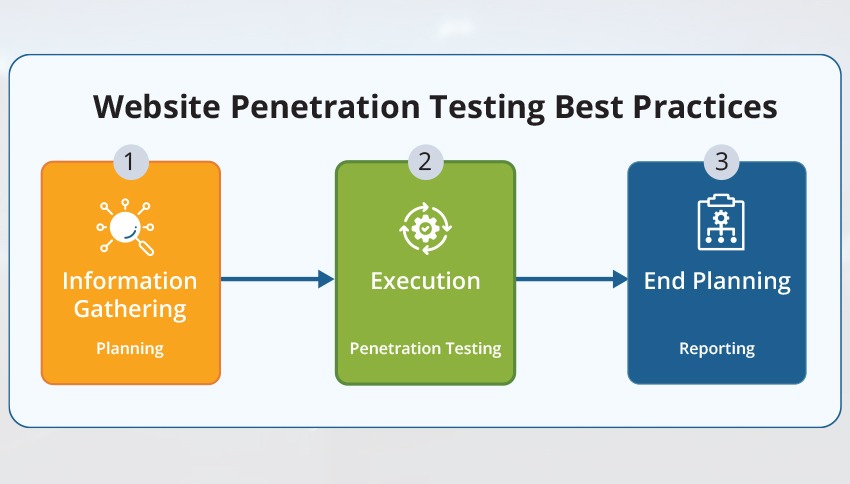
Website Penetration Testing – Best Practices
Website penetration testing primarily focuses on the environment surrounding the web application by gathering publicly available information. Cybersecurity experts identify vulnerabilities using the following steps:
1. Information Gathering and Planning
Before testing begins, the tester determines which tests to conduct and what information is needed. They collect as much data as possible about the web application, typically using open-source tools. This includes details like link structures, server types, databases, programming languages, and more.
2. Execution of Penetration Testing
With the gathered information, the tester simulates attacks to exploit vulnerabilities either by using automated or manual testing. Preferring automated tools facilitates the testing process and helps to reduce human error and complete the testing process quickly and efficiently. Whereas, manual testing can uncover the blind spots that might miss automated tools.
3. End Planning
After testing, the testers will report their findings to the IT and security teams of the organization. The findings are reviewed, and remediation actions are planned. In addition to remediating the vulnerabilities identified, organizations should also make sure they are maintaining a strong security posture. Testers should also revert any proxy settings or configurations that the changes were made to during testing.
Why Every Business Needs Website Security Testing
Conducting the website penetration testing validates the complete security infrastructure of a web application and it is essential for every business.
1. Hackers are Becoming More Advanced
As technology evolves, the malicious attackers are getting smarter. By leveraging the advanced technology they discovered the easier way to infiltrate applications. Businesses should become more conscious of their security infrastructure and stay informed about the latest updates.
2. Improves Client Confidence and Trust
Customers trust the businesses when they providing sensitive data. A robust cybersecurity posture provides confidence to customers and encourages them to share critical information.
3. Ensures Compliance with Security Standards
Website penetration testing can help businesses comply with regulations. Governments enforce strict cybersecurity laws, especially for companies handling sensitive data.
4. Protects Against Potential Cyber Threats
Any business having a digital presence becomes more vulnerable to attacks. Consistently executing the penetrating tests helps mitigate the risk of being compromised by evolving threats.
5. Identify Hidden Weaknesses
Penetrating testing reveals the flaws that might have been overlooked, allowing businesses to prioritize risks and allocate resources efficiently.
An Automated Solution
Hackers are rely on automated tools that scan for vulnerabilities across thousands of targets in minutes, exploit known weaknesses at scale, and circumvent defenses faster than human teams can respond. This modern trend has raised the stakes and shortened the window for detecting and fixing security gaps. .
To keep up with these new security demands, organizations need to adopt the same level of speed and technology in their defenses. Automated penetration testing, offers a faster alternative to traditional methods. It mimics many of the same steps a manual tester would take scanning for vulnerabilities, prioritizing risks, and generating actionable reports but does so with greater consistency and far less time.
Automation allows teams to test at scale with more frequency, fix vulnerabilities, and reduce spending, all while maintaining strong security. While manual testing still has its place for highly targeted assessments, automated solutions can cover a broader range of systems on a more consistent basis, making them ideal for ongoing security testing.
Website penetration testing is essential to protecting a web application, manual testing can often be extremely laborious, costly, and difficult to regularly incorporate into the process. Automated penetration testing changes the game by significantly speeding up the process reducing human effort, and easily streamlining the testing process that aligns with the organization’s workflows. By accelerating the identification of vulnerabilities and simplifying remediation, automation not only saves valuable time but also delivers a strong return on investment. TestWheel’s automated security testing process, ensures your web applications are safe and secure by evaluating the vulnerabilities in the application with comprehensive reports.



